 Try Hack Me
Try Hack Me
 Hack The Box
Hack The Box
 Blue Teams Lab
Blue Teams Lab
https://blueteamlabs.online/home/investigation/32
Deep Blue is an easy level defensive box that focuses on reading and extracting informtion from Event Viewer logs using a third-party PowerShell script called 'DeepBlueCLI'[1] and filtering the logs accurately.
A Windows workstation was recently compromised, and evidence suggests it was an attack against internet-facing RDP, then Meterpreter was deployed to conduct 'Actions on Objectives'. Can you verify these findings?
You have been provided with the Security.evtx and System.evtx log exports from the compromised system - you should analyze these, NOT the Windows logs generated by the lab machine (when using DeepBlueCLI ensure you're providing the path to these files, stored inside \Desktop\Investigation\.
Lets start with looking at what files are available for investigation:
First thing we need to do is open the security.evtx file and review its contents. We can do this using DeepBlueCLI (as asked) to help automatically filter the log file for specific strings of interest. To do this we need to open PowerShell within the DeepBlueCLI folder. We can do this by holding "SHIFT" and Right Click then selecting 'Open PowerShell window here'. Once this has been done, we can type the following to get an overview of the Event Viewer log:
PS C:\Users\BTLOTest\Desktop\Investigation\DeepBlueCLI-master> .\DeepBlue.ps1 .\..\security.evtxOutput:
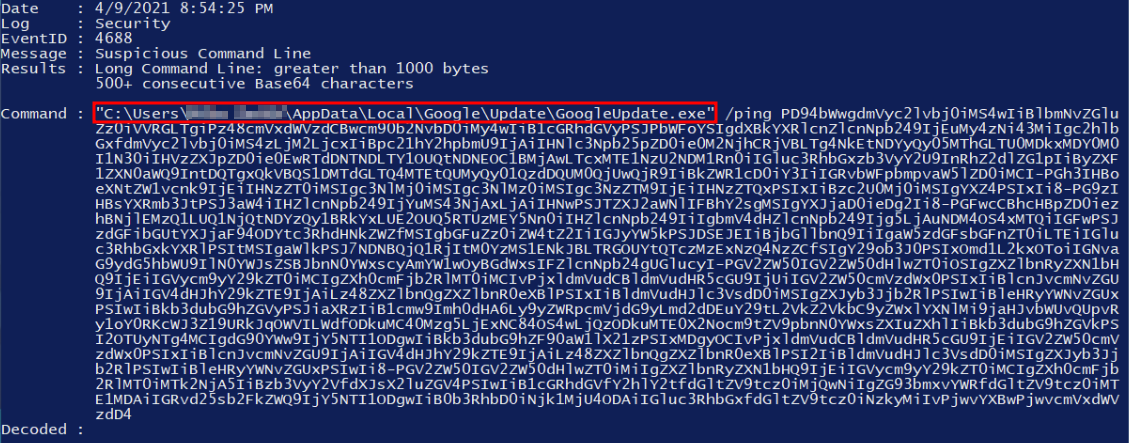
We can see the user REDACTED was using GoogleUpdate.exe that had encoded Base64 into it. Lets decode this and look at what action was performed. We will use CyberChef to see the output:
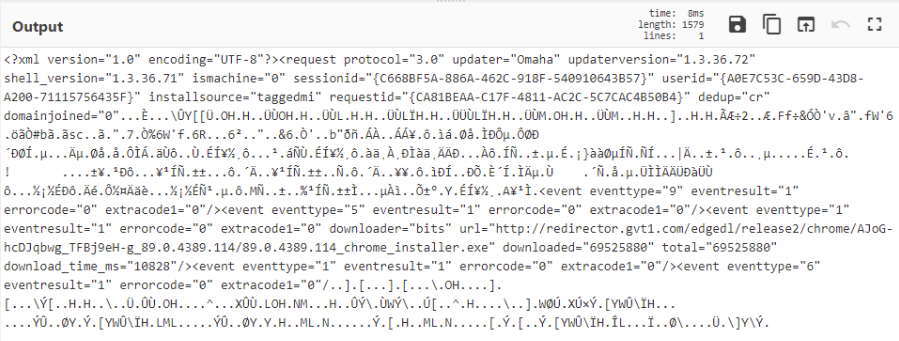
It appears an XML request was made. This doesn't appear to be suspicious to me, more just notifying the Google Update tool that it wants to download a new version to run. I could be wrong but I can't see anything more from it. Lets move onto the next question for further information.
Using the same technique from question 1 we can read through and find the log file required:
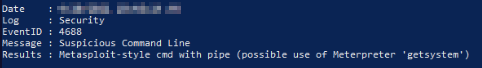
We can see a meterpreter shell was in use at REDACTED. But what is meterpreter[2]? It is a tool used to help create stable reverse shells to a victims machine. In this case, it is being used to keep a steady shell between the attacker and REDACTED's machine. We need to find out what program may have been used to leverage the shell in the first place, as I don't think it would of been a Google product, that is most likely being used to cover the real malicious program.
Still continuing from the 2nd question, we can look through further to see what may have been created or modified by that reverse shell. In this case we want to identify a suspicious service that has been added to the system:
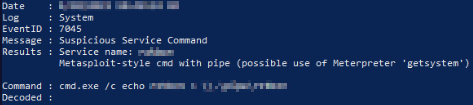
It appears that potential program called 'REDACTED' has possible commands being pipped into a service from a 'Run On Command Prompt' terminal. This may be the service being used to report back potential commands back to the hackers machine? Lets keep looking.
To answer this question we need to filter the current logs to the appropriate times. There is a lot of information, so filtering it will help narrow this down further. But why use this time frame? We can use the information we have gathered from the previous questions that a shell was created sometime before 10:48:14 AM, so we can assume that an executable may have been downloaded and run within this time frame. Lets start with filtering the logs down:
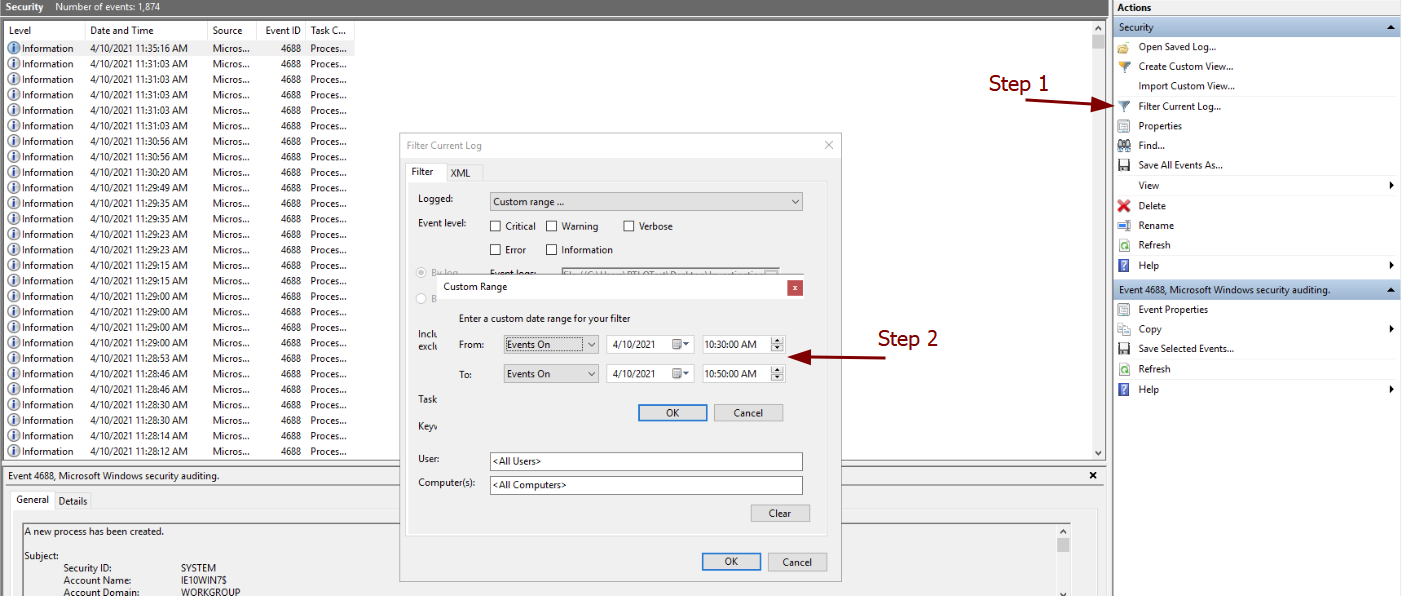
With that completed, we can see all event logs between 10:30 AM and 10:50 AM on the specific day. Going through each individual log we are looking for Downloads, so for my first sweep I want to focus on anything within the 'Downloads' folder for the user. I can do this quickly using the 'Find...' function on the right hand pane. The results:
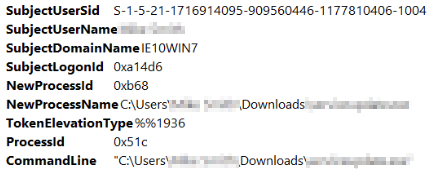
Bingo. Looks like we can see REDACTED downloaded a program called 'REDACTED'. This could be the questionable program. The most notable thing is that this program was downloaded roughly 2 minutes before the attack occurs. About 40 seconds after the download we can see some logon events, which could be the reverse shell connecting:
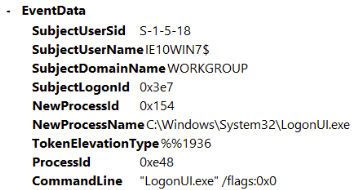
Persistence is the key to controlling the machine. Using the same filtering performed in the previous question we can narrow this down and look for user account creations with the 'Find...' feature again. We have found our first potential user account:
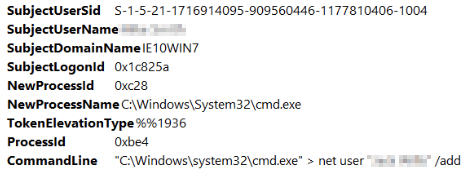
Looking through, it appears the hacker may not be comfortable with Windows, as they are trying to privlege escalate but can't seem to get the command correct for it. Maybe this isn't the user account in question. Lets look for the next account creation:
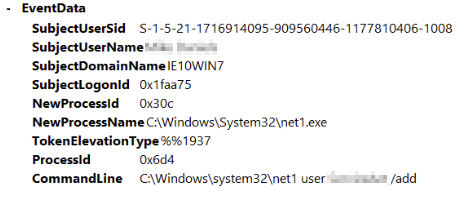
Lets verify this by seeing if they were able to privlege escalate this account correctly:
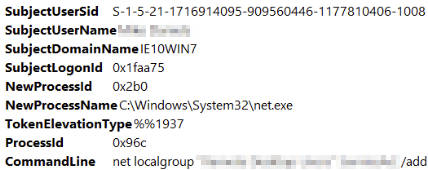
We can also verify by the next entry they were able to add this user account to accept RDP and then login with this account.
We know the first group this was added. We just need to roll back 1 or 2 events and we should see the other local group, otherwise we can search for the command net localgroup with the 'Find...' and we should see it easily:
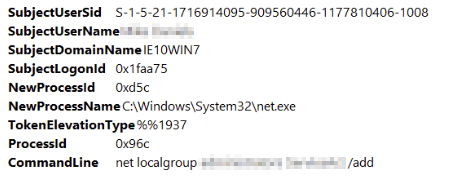
[1]https://github.com/sans-blue-team/DeepBlueCLI
[2]https://www.offensive-security.com/metasploit-unleashed/meterpreter-basics/
It appears that employee Mike Smith may have accidentally downloaded a malicious software, serviceupdate.exe, without realising this. Once the user ran this program with admin access, the software was then able to leverage a reverse shell, via meterpreter, by adding a custom service being named rztbzn. Once the shell was established as 10:48:14 AM on April the 10th 2021, the attacker was able to create a new account, ServiceAct, trying to hide it as a regular service account for the machine. Once this account was created the attacker was able to privilege escalate this account to join the local groups Administrators and Remote Desktop Protocol. This has allowed for the attacker to backdoor into the device without appearing to have compromised the machine in doing so and potentially bypassing any event triggers that may be in place within the company and SIEM.
To resolve this issue, I believe the first thing to be performed on this device is locking down the machine to an offline presence only, removing the malicious software serviceupdate.exe. Removal of the service rztbzn is next followed by deletion of both user accounts Jack Wills and ServiceAct.
Or you could wipe the machine and restore a backup if it is available.
To prevent this from reoccuring admin access will need to be removed from the user account Mike Smith to ensure that anything downloaded and executed requiring admin access is notified and installed via the IT team. This could help mitigate any chance for this breach occuring again.
This is a great beginner level room to introduce the user into reviewing and extracting necessary information from Event Viewer logs. It also helps introduce Third Party scripts to simplify this further. The skills learnt from this room can also be carried across to other IT roles for day to day use in truobleshooting and information gathering. Thank you for spending the time reading through my walkthrough.