 Try Hack Me
Try Hack Me
 Hack The Box
Hack The Box
 Blue Teams Lab
Blue Teams Lab
https://blueteamlabs.online/home/investigation/57
Ducker is a medium level box that focuses on operating and understanding how Docker operates on machines, as well as how to access individual Docker instances as required and privilege escalation if improperly configured.
“Congratulations on passing the first level of interview! Time for a practical test before we can take you onboard.” -Mark
Let's start by explaining what Docker is. Docker[1] is a tool used to create 'containers' on a system to house their own programs/binaries and systems. The best way of thinking about it is to think of each container as a VM. You can essentially have multiple VM's (containers) on a machine each for their own use. Why would you do this? Well to help segment items, and the belief of added layer of security. The second point is not always true, which we may see later on in this box, but misconfiguration of Docker is a common trope that can lead to many issues on compromised machines. The purpose of this room, however, is to just learn about the different areas and how Docker functions.
So for the first question, we can simply run a switch in docker to find the version number:

What is a container[2]? Well outlined above it is a VM within a machine, which is sort of correct. In the URL I reference, Docker states that VMs and containers are similar, but operate on a different level due to a VM relying on the hardware, whilst a container relays more on the OS of the machine. What does this mean? Well containers are easier to move around from 1 system to another as it doesn't require any of the hardware specifications set in a VM, it only needs the same OS. So you can move 1 container from a Windows 10 machine, to another without having to worry about the hardware, you only need to ensure the OS is the same. This also has the benefit of having multiple containers operating on the 1 system and ease of moving them between systems.
So knowing what a container is (which I hope I understood it correctly), we now need to use Docker to list containers that are on the system. Similar to Linux, Docker has similar commands and you may need to list all the containers to view it. If you wanted to see a full list of commands you can use the following:
docker container --helpWhen you have found the correct command you should find the answer like below:
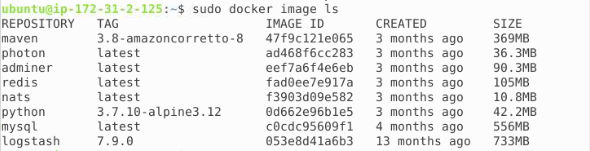
What is a bridge network[3]? This Link Layer device helps forward traffic between the network segments, which for Docker, allows for containers to be isolated allowing for more secure networks/containers. This can be modified by adjusting the rules set by Docker as it is purley a software driver set by Docker in this case. You can get hardware Link Layer devices but Docker is just software, so it is built in. A network within Docker does NOT need to be a bridge network. There are different types (overlay, host, macvlan, etc.) but we won't be touching on them in this example. For additional information please refer to the Docker website linked in this paragraph.
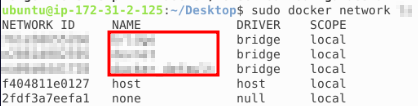
You can view the networks set within Docker by using the correct switches and then see which specific driver that network is using:
We can expand on specific containers to see their. First we need to find the container in question and then we can expand on it using the container:
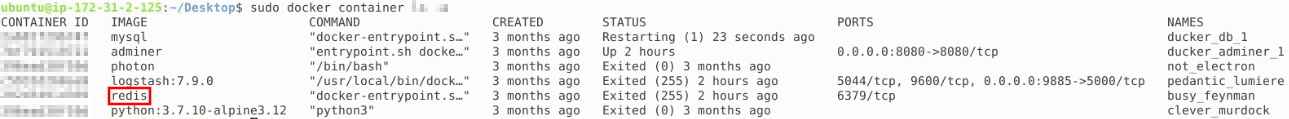
Once we have the correct container ID we can then view the container with inspect. When we type in the correct command we get the following output with the answer located:
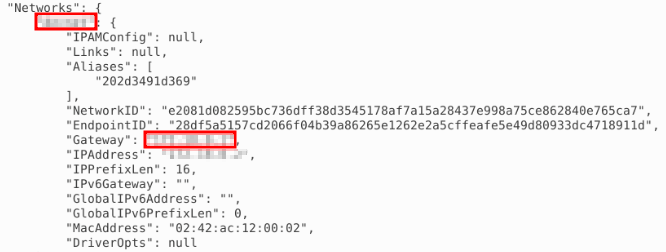
We need to find the container ID for pedantic_lumiere:
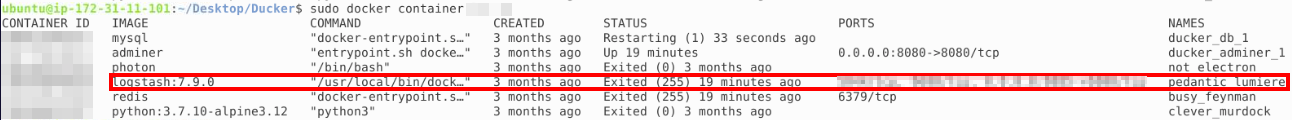
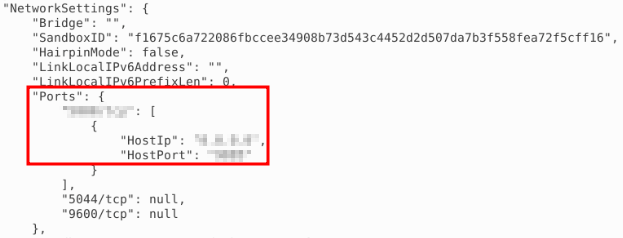
With the ID we can inspect the configuration of the container and find the answer:
We need to understand what is happening in the Dockerfile[4] file to understand what will be executed. Docker uses its own instructions to perform specific tasks. Once have an understanding on what is occuring we then need to type in what file is being used with the specific command being run. No image for this question will be available as this will easily answer the question, but you need to read the Dockerfile in question to recieve the answer.
If we look around the secrets folder in the Linux terminal, we can locate a hidden file with some odd permissions:
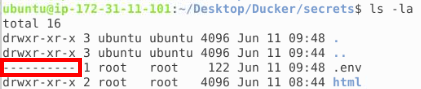
When we try to use chmod we are informed that it isn't installed on this box. So we can't read, write or change the file how can we access it for information? This is where Docker may allow us to leverage a container to potentially view the content. First we need to see how we can operate a Docker container to do this. We know the Dockerfile that has the information, but which container is running this Dockerfile? We can use cat to view the contents of the Dockerfile:
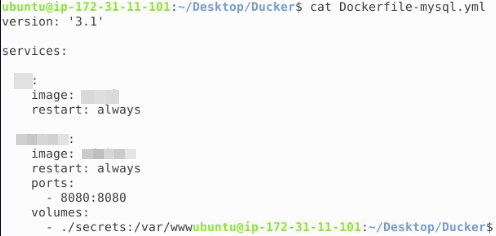
We can see 2 images referenced and if we review the previous images of the containers listed, we can see only 1 of these images currently functioning. Lets log into the container with the username information:
sudo docker exec -it REDACTED /bin/shOK. We have entry into the container. We navigate back to 'secrets' and we don't have the ability to change the permissions. We also can't sudo to do this. What now? We can run any Docker command in sudo, so maybe we can log into this containter with a root account? Lets try and see what happens:
/var/www/html $ exitNow with the proper access we can navigate to secrets and change the permissions to find the answer we require:
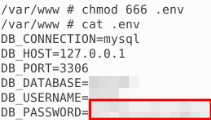
We can use the --help switch to view what switches are available within specific command's. Doing this within the contianer command we can find the answer:
docker contianer run --help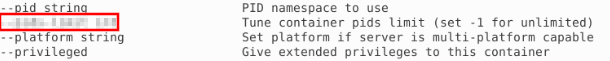
Researching what this is, I found a great article by OWASP detailing how to properly secure your Docker containers. You can view this here. You can find the answer within that webpage, but I recommend reviewing all of it for a greater understanding on security within this program/binary.
This is asking to give the command needed for Docker to pull the hashsum mentioned. We can find the necessary switches using --help. When we find the correct switches it will look like:
docker REDACTED mysql@sha256:68b207d01891915410db3b5bc1f69963e3dc8f23813fd01e61e6d7e7e3a46680Once again, we need to locate the ID of the container so we can use the necessary switches to read the configuration file of the container. We can then leverage grep to search for any item with the word 'log' in it:
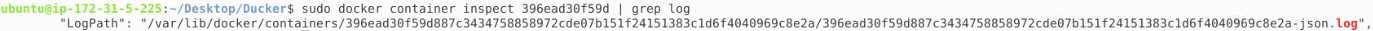
[1]https://docs.docker.com/
[2]https://www.docker.com/resources/what-container
[3]https://docs.docker.com/network/bridge/
[4]https://docs.docker.com/engine/reference/builder/
A very informative room on how Docker and its components operate, and how we can review current configurations on the containers. I found this box to be medium difficulty as I don't use Docker all that often, but am now looking into implementing it into my network. If I do maybe I will release my tutorial on how I did so and my attempts at hardening it. Who knows... so much to learn, so little time.
Thank you for reading.