 Try Hack Me
Try Hack Me
 Hack The Box
Hack The Box
 Blue Teams Lab
Blue Teams Lab
https://blueteamlabs.online/home/investigation/73
Print is an easy level box focsued on reviewing Event Viewer logs and Wireshark PCAPNG files.
Our security team came to know about the latest exploit on Windows Print Services. As you are part of the detection team you were asked to submit the artifacts to create detection rules. The red team helped to create a vulnerable setup and a working exploit.
As a blue teamer, it's your turn to analyze the logs to identify the artifacts and submit them to the SOC team.
Like always, I like to show what files we have to investigate with:
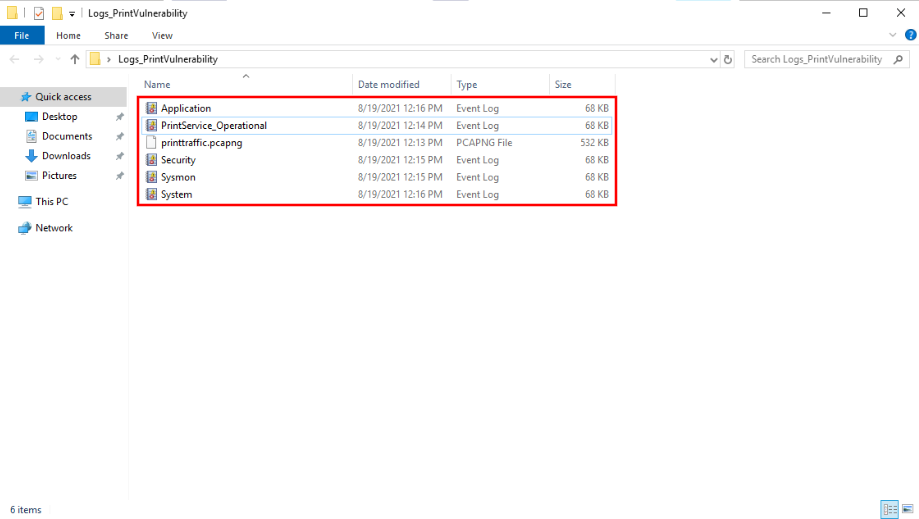
We can see that we have 5 Event Logs and 1 PCAPNG file. For the first question we just need to open the System Event Log and locate the section displaying the Domain:

Wireshark [1] has a built in tool that will allow us to easily select all SMB packets:

With this feature enabled, we can see all SMB traffic and we can then follow the TCP stream [2] for SMB. We can find the results with the file transferred below:
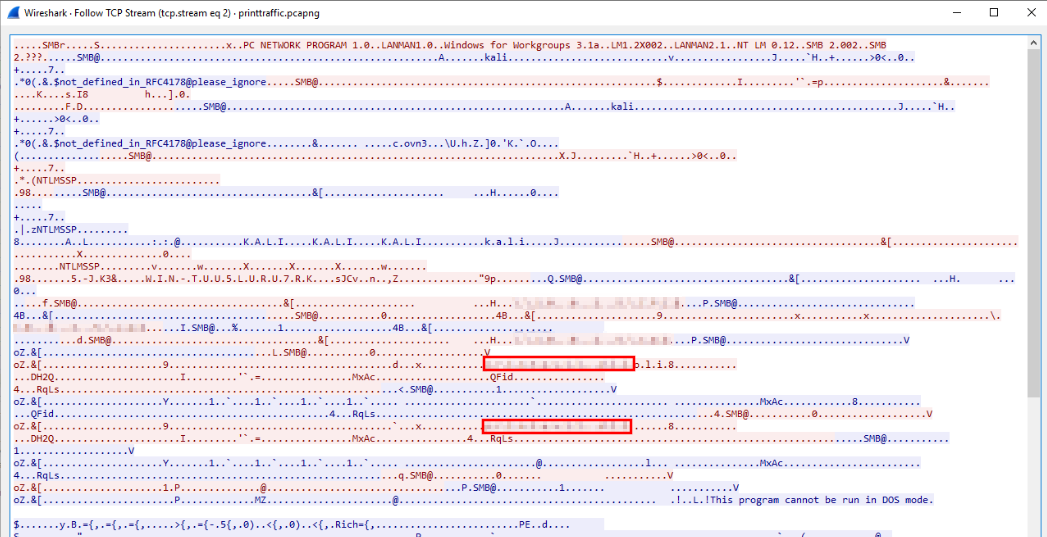
We can confirm this with searching the PCAPNG file for the string "REDACTED":

With the required information already open, we just need to read the output again and we should be able to see the IP:/File location:

With the information gathered we know the attackers IP address, we just need to narrow down the potential port used to access the machine. If you know the common ports used, you know it could be a common port that can be used to bypass any firewall. We can locate this information in both Wireshark and the System Event Viewer:

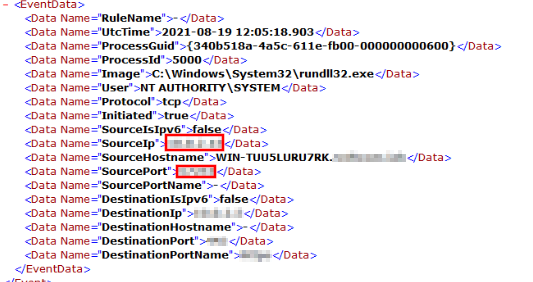
We now need to filter each Event Viewer log for the following information stated. Once we have input the correct filtering options we can then find the necessary information like below:
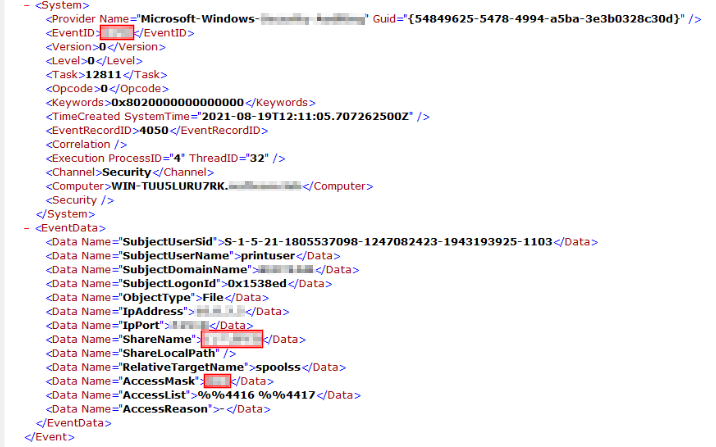
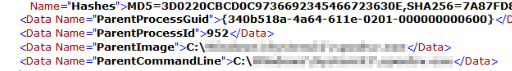
Now we need to filter a specific Event Log to find the executable. Within the Event Log details we can find the specific line related to the Parent Image and Parent Command Line:
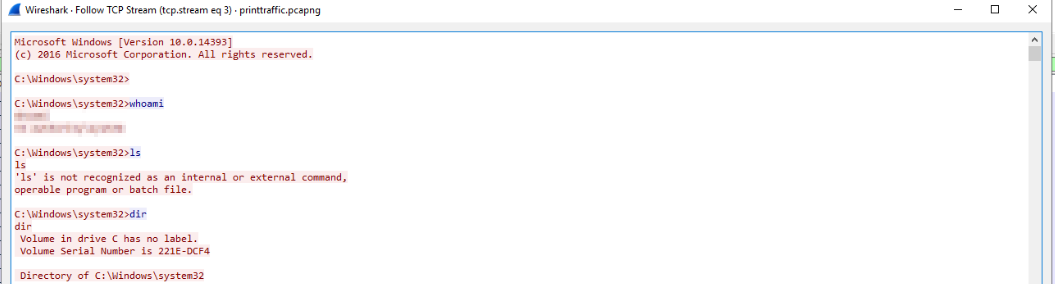
Thanks to all the information we have gathered from the previous questions (Attackers IP, Port) we can now easily filter Wireshark [3] for this information and then follow the TCP stream as mentioned earlier to see all input/output from the reverse shell:
[1]https://www.wireshark.org/docs/wsug_html_chunked/ChIOExportSection.html
[2]https://www.wireshark.org/docs/wsug_html_chunked/ChAdvFollowStreamSection.html
[3]https://www.wireshark.org/docs/wsug_html_chunked/ChWorkDisplayFilterSection.html
Mahcine WIN-TUU5LURU7RK has been compromised via an attacker who was able to upload a malicious .dll to the machine. Once the attacker was able to connect to the machine via Port 443, they could then leverage the malicious file to escalate privleges and assume administrator control via account system. Best course of action is to change the password information for SMB, remove any anonymous login if available and remove the malicious file. Due to the severity of access I would even recommend re-imaging the machine to ensure any persistence placed on the machine has been removed permanently.
Very simple room that helps users dip their toes into viewing Event Logs and Wireshark PCAPNG logs, as well as learning commands and features to try to filter these logs.